Info Gathering
80 - HTTP
Visiting the web app on port 80 returns a login page for an application called CODIAD.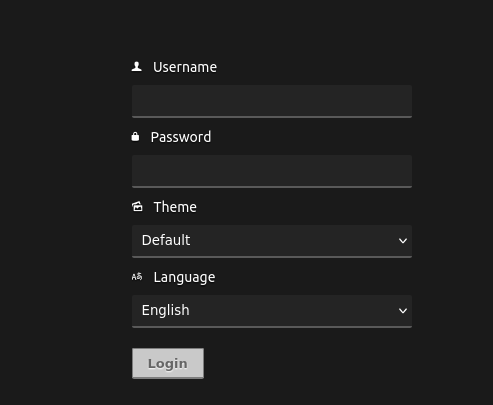
admin:admin.
Foothold
CODIAD is a web‑based IDE framework. Just like how a desktop application would, I can upload any file I want. I then check what public exploits are available usingsearchsploit:
LPE - capability
During local enumeration, I identified thecap_dac_override+ep capability on the tar binary.
cap_dac_override+ep is a capability that ignores the permissions of a file and basically bypasses it. With tar, I can get a copy of any file, archive it, and then extract it to replace the original. /etc/passwd is my target file in this case.
First, I’ll archive /etc/passwd and then extract it into my current directory:
openssl to generate a password hash:
su into the alternate root account.